In today’s fast-paced digital world, privacy is often compromised for convenience. As more personal information is shared online, safeguarding one’s data has become an ongoing challenge. The surge of data breaches, surveillance, and targeted advertising raises important questions about online privacy. To address these concerns, a revolutionary approach to digital security has emerged, offering users the ability to take control of their personal information like never before. This technology, powered by cutting-edge encryption and decentralized systems, ensures that individuals can engage online without worrying about prying eyes or unauthorized access to their data. The concept behind this new wave of privacy-first technology is rooted in the idea that individuals should be the sole custodians of their personal information. Rather than relying on centralized platforms, which can be vulnerable to hacking or misuse, this approach leverages decentralized networks. These networks operate on blockchain-like structures, where data is dispersed across multiple nodes, making it nearly impossible to track, manipulate, or access without proper authorization.
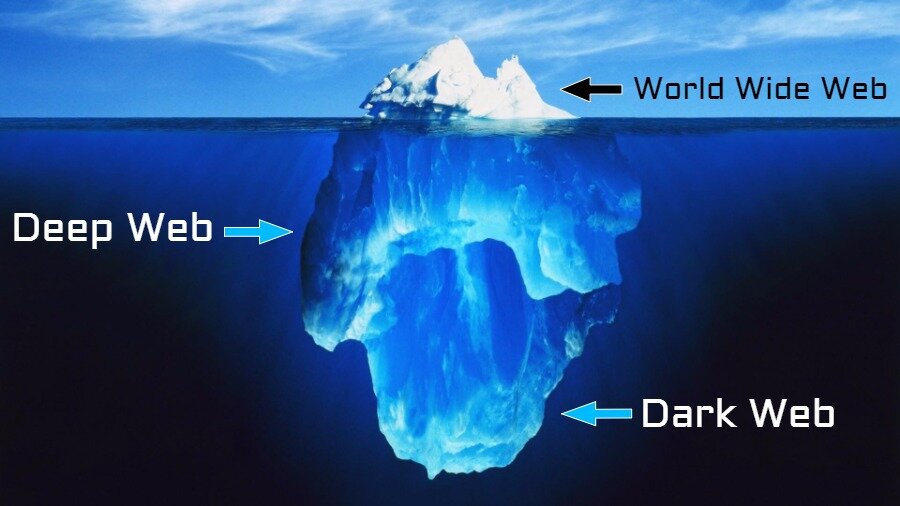
This not only strengthens security but also promotes trust and transparency, as users are in control of their digital footprint. Encryption lies at the heart of this system, protecting user data with state-of-the-art cryptography that ensures that even in the event of a breach, the information remains unreadable and useless to intruders. Every communication, transaction, or exchange of information is encrypted, adding layers of protection that prevent unauthorized access. This encryption is further enhanced by the use of advanced algorithms and private keys, which act as digital signatures to verify the authenticity of the data without exposing it to external risks. One of the key features of this technology is its ability to enable anonymous browsing and secure peer-to-peer communications. With the rise of digital surveillance, users are often tracked across websites and platforms. This new privacy-first system nullifies these tracking methods by masking the user’s identity, location, and online activities. It gives people the freedom to explore the web without the constant fear of being monitored or having their personal preferences exploited.
The shift towards privacy-first technologies is not just about preventing external threats; it is about empowering users to regain control over their digital lives. Archetyp darknet opting for platforms and tools that prioritize security and anonymity, users can break free from the endless cycle of data exploitation that has become synonymous with the internet. In doing so, they ensure that their personal information remains their own, shielded from corporate and governmental entities seeking to harvest and sell it. As this technology continues to evolve, it promises to redefine how we experience the internet. What was once a space filled with insecurity and data vulnerabilities is rapidly becoming a more private, secure, and user-centric environment. The future of online privacy is one where individuals no longer have to sacrifice their personal data for convenience, but instead can navigate the digital world confidently, knowing their privacy is protected at every step. This marks the beginning of a journey towards a safer, more secure online experience, where privacy is not a privilege, but a right.







